The Role of Secure Web Gateways in Modern Cybersecurity
Organizations today are confronted by a constant surge of cyber threats as digital transformation, remote work, and cloud reliance reshape the modern business landscape. Protecting against data breaches, malware, and ever-evolving web risks means organizations must secure internet access for employees and assets, whether on-site or remote. This is precisely where Secure Web Gateways (SWGs) prove their value, offering powerful, policy-driven protection at a critical access point to the internet and web-based resources. Solutions like Versa SGW set a new standard, helping organizations proactively defend their networks while ensuring productivity and compliance remain uncompromised. Many organizations now recognize SWGs as central to a layered security strategy. By functioning as both enforcement points and compliance gatekeepers, they provide the robust visibility and controls essential in a perimeter-less world. But as threats grow in sophistication—and as cloud and hybrid environments become the norm—the right SWG platform can make the difference between safe, compliant operations and being the next headline data breach casualty.
Understanding Secure Web Gateways
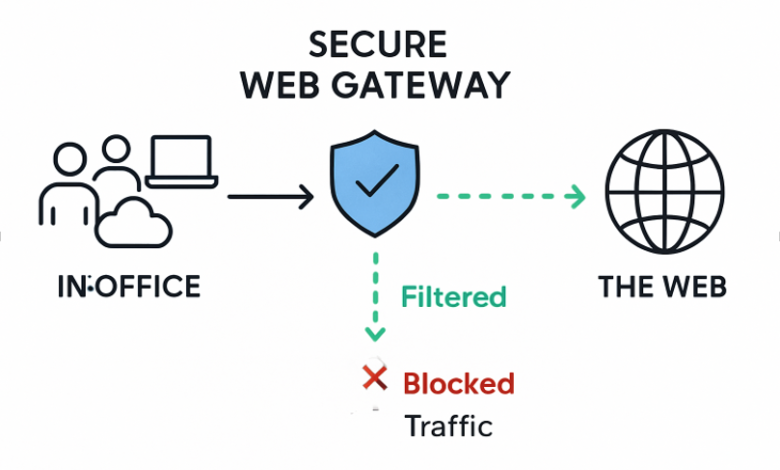
Secure Web Gateways act as organizations’ frontline defense against internet-borne threats. These solutions scrutinize, filter, and control all inbound and outbound web traffic, providing companies with a vital barrier that shields internal networks from malicious content. Unlike traditional firewalls, SWGs offer deep content inspection, address encrypted connections, and enforce granular security and compliance policies tailored to organizational needs. The necessity of SWGs becomes more apparent as cybercriminals increasingly rely on sophisticated means such as embedded malware in legitimate sites, advanced phishing lures, and zero-day exploits. By continuously inspecting traffic in real time, SWGs defend networks before threats can exploit vulnerabilities—regardless of whether users are in the office, working remotely, or accessing cloud resources. Comprehensive SWGs don’t just block known threats; they also help prevent data loss and unauthorized access to business-critical information. Organizations with advanced web filtering, SSL decryption, and strong data loss prevention measures are far better positioned to manage high-stakes compliance obligations and regulatory requirements.
Key Features of SWGs
- URL Filtering: SWGs permit or block website access based on categories, security reputation, or specific policies. This helps prevent users from visiting unsafe or non-compliant sites, mitigating exposure to productivity drains and cyber risks.
- Malware Detection and Sandboxing: Robust SWGs employ real-time malware scanning, threat intelligence feeds, and sandboxing of suspicious payloads. These layers stop known and unknown threats before they can impact endpoints and infrastructure.
- Data Loss Prevention (DLP): DLP policies in SWGs monitor outbound web traffic, blocking sensitive information (such as personal data or intellectual property) from leaving the organization in an unauthorized or unprotected state.
- Application Control: SWGs allow organizations to recognize and manage web and cloud-based applications. By controlling application traffic, organizations minimize risks associated with unsanctioned or unsafe apps, often called “shadow IT.”
- SSL/TLS Inspection: SSL/TLS inspection is critical, as most web traffic is now encrypted. SWGs decrypt, inspect, and re-encrypt traffic, exposing hidden threats while ensuring privacy and regulatory compliance.
See also: Unveiling the Unparalleled Power of AI Image Detection Technology
The Importance of SWGs in Cybersecurity
The advent of hybrid and remote workforces and a substantial shift toward SaaS and cloud platforms have dissolved traditional network boundaries. This new reality underscores why SWGs have become indispensable. By serving as a centralized control point, SWGs deliver policy consistency, deep visibility, and streamlined compliance—regardless of user location or device. Additionally, SWGs defend organizations from zero-day threats and sophisticated phishing campaigns. Given the rapid evolution of cyber adversaries, relying solely on endpoint or basic perimeter defenses is no longer sufficient. Businesses with comprehensive SWGs experienced significantly fewer incidents involving data exposure and successful web-based attacks.
Recent Developments in SWGs
As organizations trust more in cloud platforms, SWGs themselves are evolving. In June 2024, Broadcom’s Symantec Cloud Secure Web Gateway received FedRAMP authorization—a key milestone for U.S. federal agencies adopting cloud-based defenses during digital migration efforts. Cloud-native SWGs like this show how scalability, ease of deployment, and regulatory rigor now blend in next-gen security services. Another landmark came in November 2023 with Open Systems’ launch of a comprehensive Secure Web Gateway as a Service, integrating advanced threat protection and secure cloud access. This reflects the rise of Secure Access Service Edge (SASE) architectures, where SWGs unite with zero trust, SD-WAN, and identity services for a seamless, centrally managed experience.
Implementing SWGs in Your Organization
- Assess Current Security Posture: Audit existing security controls, identify vulnerabilities, and understand the business’s risk profile, focusing on web exposure and cloud app usage.
- Define Security Policies: Set clear internet usage rules, data protection mandates, and incident response procedures tailored to operational needs and regulatory demands.
- Choose the Right SWG Solution: Evaluate SWG providers’ ability to scale, integrate with hybrid or multi-cloud environments, and provide unified visibility and management. Ensure support for remote, mobile, and office-based employees.
- Educate Employees: Offer regular, actionable training on securely using web services and recognizing emerging threats. Awareness remains one of the strongest defenses against human error and social engineering attacks.
- Monitor, Evaluate, and Update: Continuously track SWG performance, adapt policies as new threats emerge, and validate compliance with internal and external requirements. Ongoing improvement is essential as cyber risk landscapes change rapidly.
Conclusion
The accelerating pace of digital innovation—paired with the persistence and creativity of threat actors—makes Secure Web Gateways an anchor in any robust security program. With capabilities far beyond traditional filtering, modern SWGs underpin safe internet access, enforce critical compliance, and safeguard confidential assets. Organizations can confidently pursue growth, remote work, and cloud expansion by adopting a future-ready SWG strategy, knowing their digital perimeters remain protected.